YES! Particularly if you’re a small/micro business. Bandwidth and internet speeds are most precious in this era of the ‘cloud’. If you’re a smaller business, you don’t have bandwidth to go around. Being able to filter what your users can go to can greatly increase your capabilities to get work done. Equally important, businesses need […]
Continue reading6 Known Angles Cyber-Criminals Exploit
As long as businesses continue to operate and make money, cyber-criminals will look for ways to break in, exploit weaknesses, and steal. To defeat them, you need to find the angles they use to exploit your systems. Here are 6 Known angles cyber-criminals exploit. Threat #1: STOLEN DEVICES Hackers physically stealing equipment with sensitive data. 80% […]
Continue readingSiri, Echo, Alexa, Google Home, Cortona, Are Your Digital Assistant’s SAFE to use?
By now all have heard of the security risks involved with these devices. Let’s think… How are they supposed to know ‘when’ to listen if they’re not listening all the time? They are several ways security firms have shown to infiltrate these devices at several levels, some easier than others but all vulnerable, regardless […]
Continue readingClever Scam for the tired and the less-than-experienced to fall for. BE CAREFUL!!
Another Clever Scam for the tired and the less-than-experienced to fall for. BE CAREFUL!! This can be done over text or email. The ‘Victim’ receives a text or email (official looking of course) asking if you requested a password reset on your account, and if you didn’t reply with the word ‘STOP’. (or something similar). […]
Continue readingStruggling with Securing Sensitive data?
Why do so many companies struggle with securing sensitive data? Many of today’s business processes are done digitally, so why it is that data protection and cloud security remain such a challenge? A large reason why is because as more companies become aware of data security threats, cyber-criminals adeptly adjust just as fast, refocus their […]
Continue readingThe KRACK ATTACK
This latest attack, or hack, is more ‘device’ related than network related, so it is important that all devices be updated as well as networks. This Vulnerability can allow and attacker to use a ‘Man in the Middle’ type connection to gain access to all your information sent to and from a website (login information) as […]
Continue readingHow To Tell If A Charity Is A Scam
While there are legitimate charities and fundraising efforts, there are also reports of scam artists creating fake charities to con you out of your money and information. The Federal Trade Commission has good advice on warning signs that could indicate a bogus charity. Here is a TOP TEN List of the best tips we’ve […]
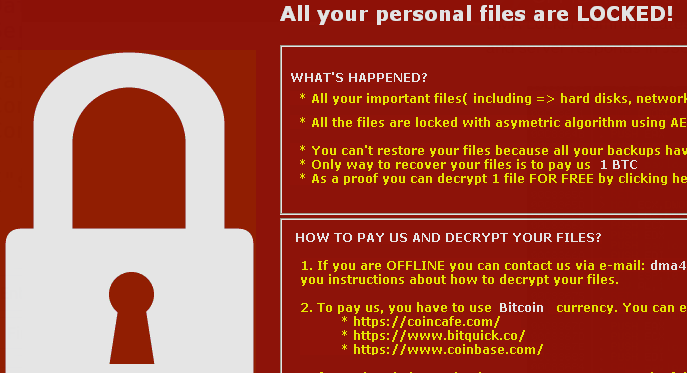
Continue readingYet Another Ransomware
Yet Another Ransomware Another ransomware found in the wild called DMA Locker.Seems these are popular and gaining in frequency of appearance. The ability for these infections to extort money quickly is more effective than one may think. How much would you pay to get your data back? Ransomware remains
Continue readingAdobe FLASH Type Confusion Vulnerability
Over the weekend a new Ransomeware type attack was discovered to leverage vulnerabilities in adobe Flash player. There are still MANY sites on the web that use this player. Game sites Video Streaming Sites, Etc. Flash has over one billion users, so odds are you are affected by this update. Be certain not only your […]
Continue readingNew Vulnerabilities in Popular WordPress Plugins
In case you missed the news release about the high profile plugin vulnerabilities on Word Press, we would like to bring them to your attention now and encourage you to update to the latest version immediately if not sooner.
Continue reading